Permissions
The permission system is the core infrastructure of commercial software. Through refined permission control, it can effectively prevent data leakage and unauthorized access, ensuring the integrity and security of the system and data. Momen provides a permission management system based on Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), supporting flexible and fine-grained permission configuration.
Core Concepts
- Role: A collection of users, where permission control is achieved by assigning roles. A user can have multiple roles, and the user’s permissions are the union of all roles.
- Data Permission: Precisely controls the database table content that a role can access or modify, including table-level, column-level, and row-level permissions.
- Action Permission: Controls the actions a role can perform (APIs, Actionflows, payments, etc.).
.png)
Configuration Process
Access Permission Management System
Go to “Settings” and enter the “Permission Management” module to start configuring project permissions.
Manage Roles
The system has two built-in roles:
- Logged-in User: All logged-in users are automatically assigned this role
- Anonymous User: Users who are not logged in
In the editor, developers have super administrator privileges and can access and modify all data in the database.
Developers can create custom roles based on business needs. Different project versions have different limits on the number of roles that can be created:
- Free Plan: 0
- Basic Plan: 1
- Pro Plan: 10
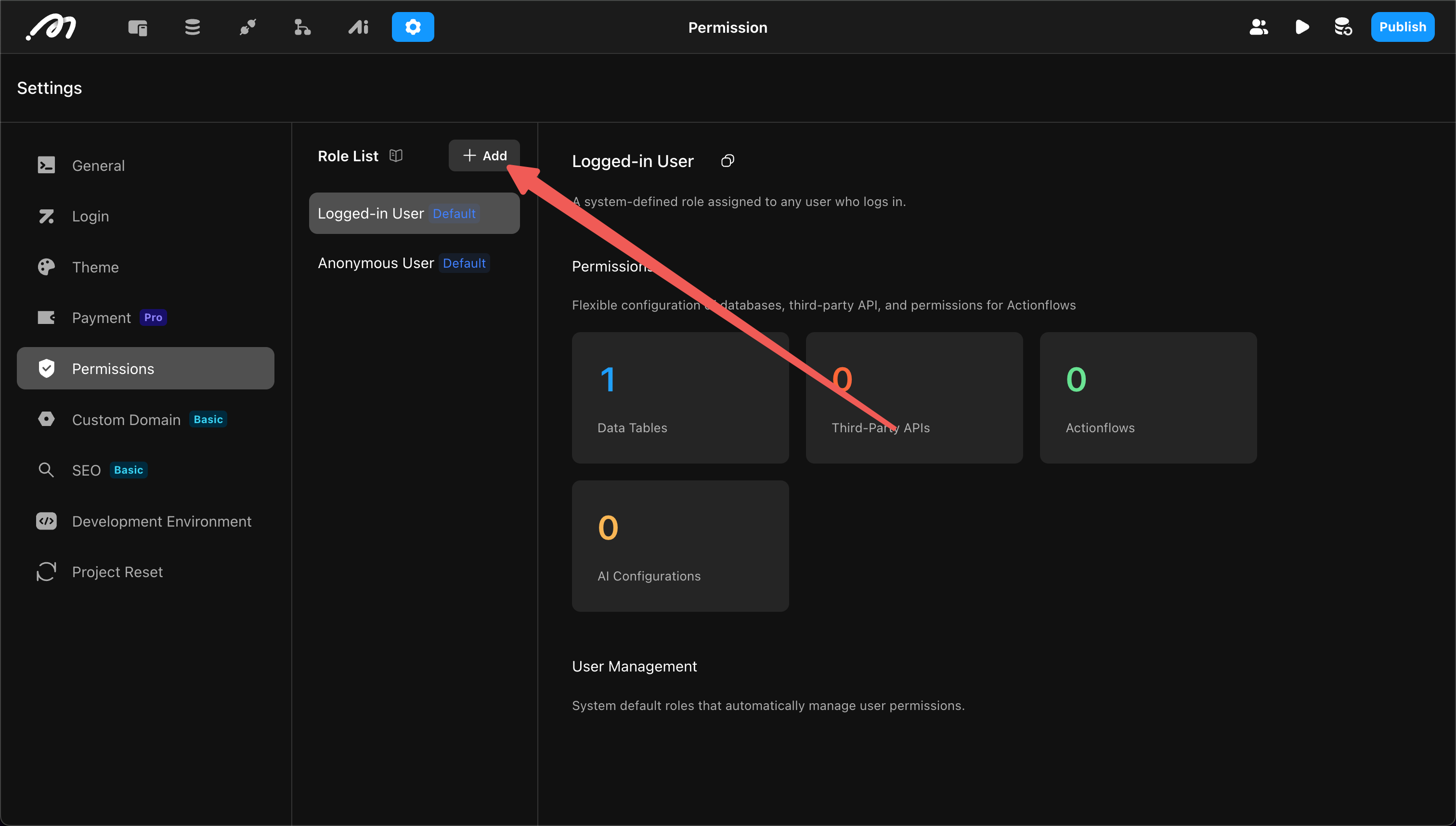
Click the “Add” button to create a new role and set the role name.
Once the role name is deployed to the backend, it cannot be changed. Please name carefully.
Configure Data Permissions
Data permissions are divided into three levels, configured from coarse-grained to fine-grained:
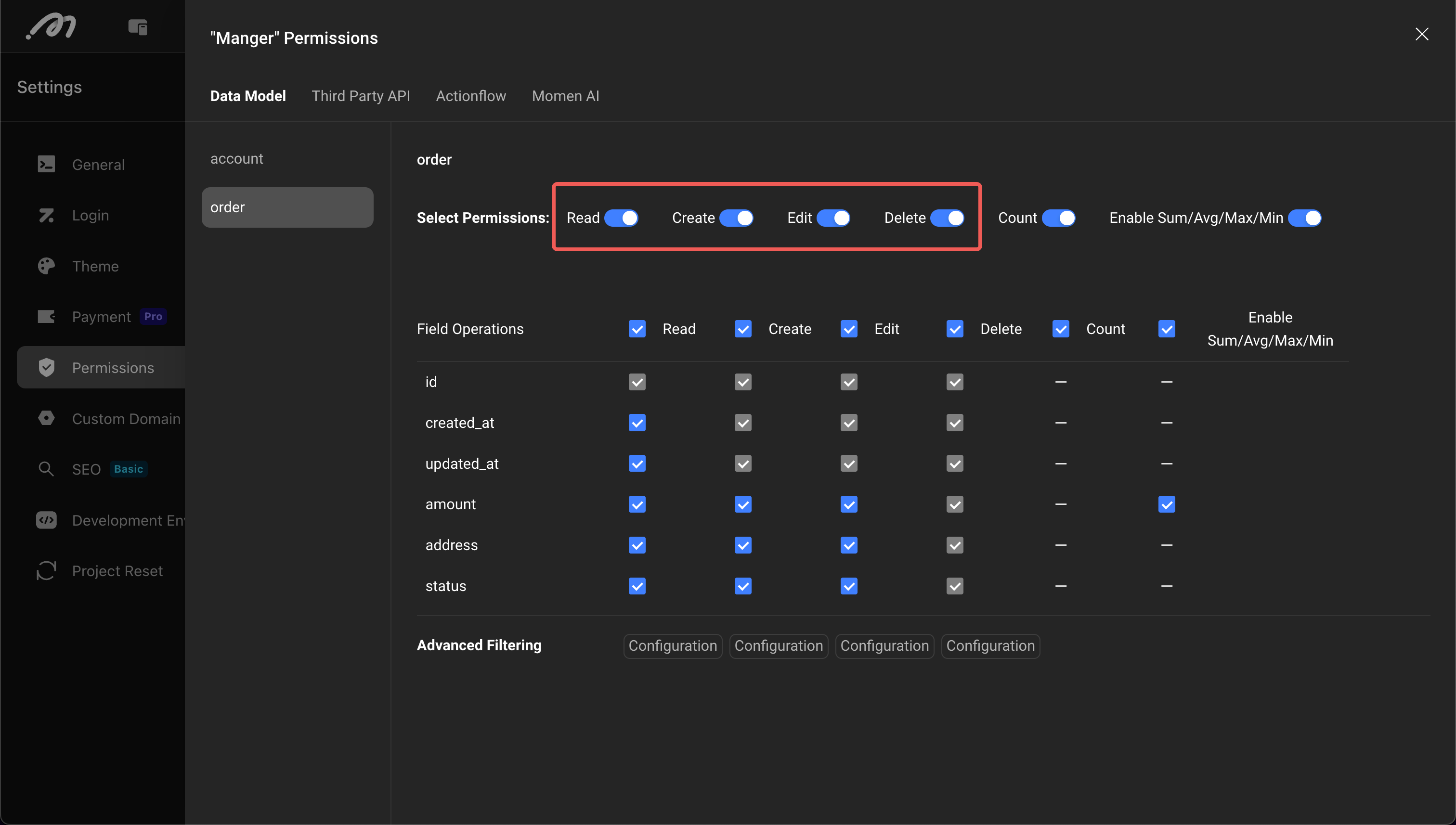
Table-level Permission Configuration
Controls the CRUD permissions for the entire table, as well as the query permissions for aggregated data (count, sum, average, etc.) of that table.
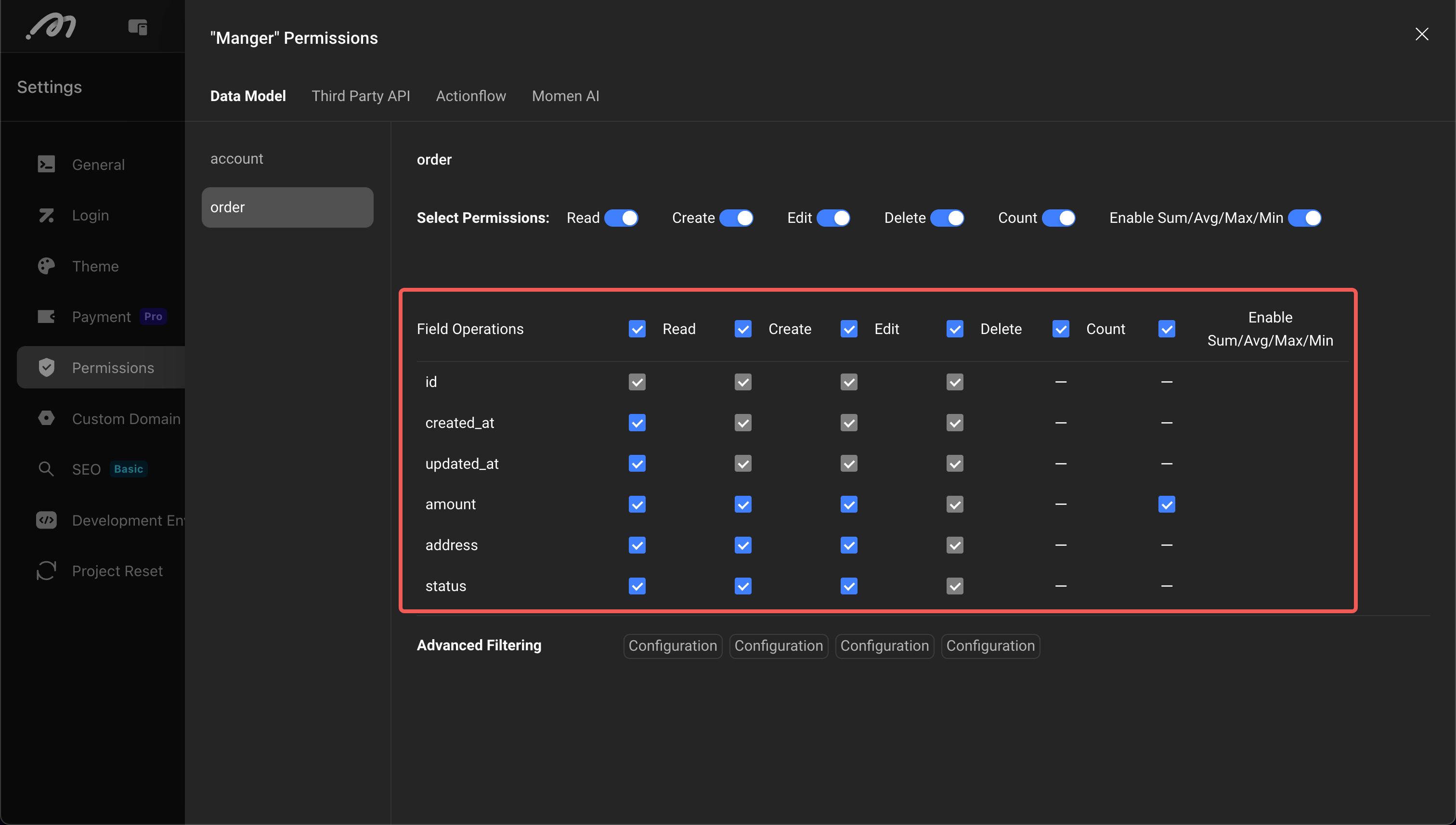
Column-level Permission Configuration
Configures the CRUD permissions for specific columns in the table, achieving field-level permission control.
Row-level Permission Configuration
Achieves the most fine-grained permission control through conditional filtering, such as configuring business rules like “users can only update orders they created”.
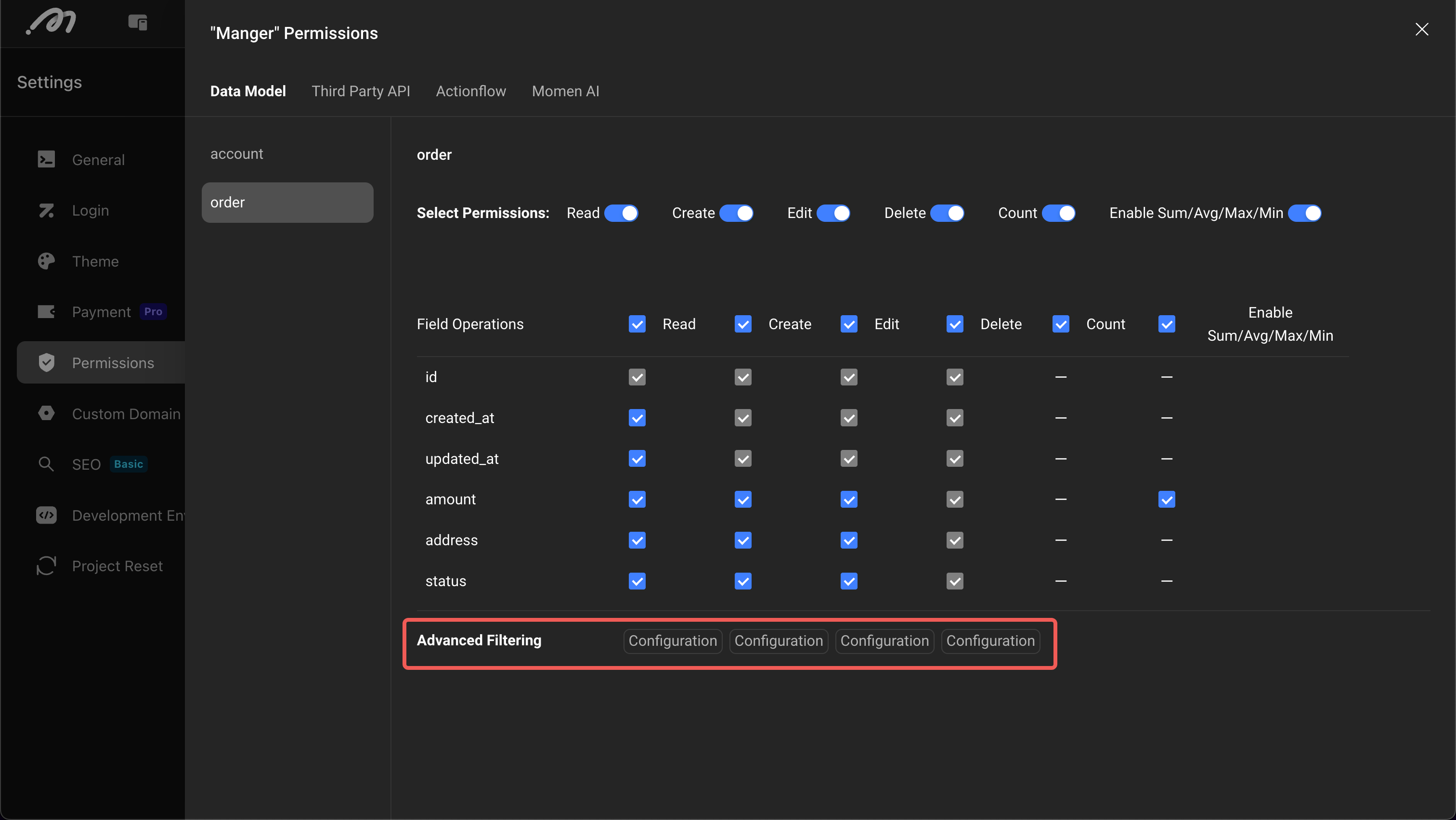
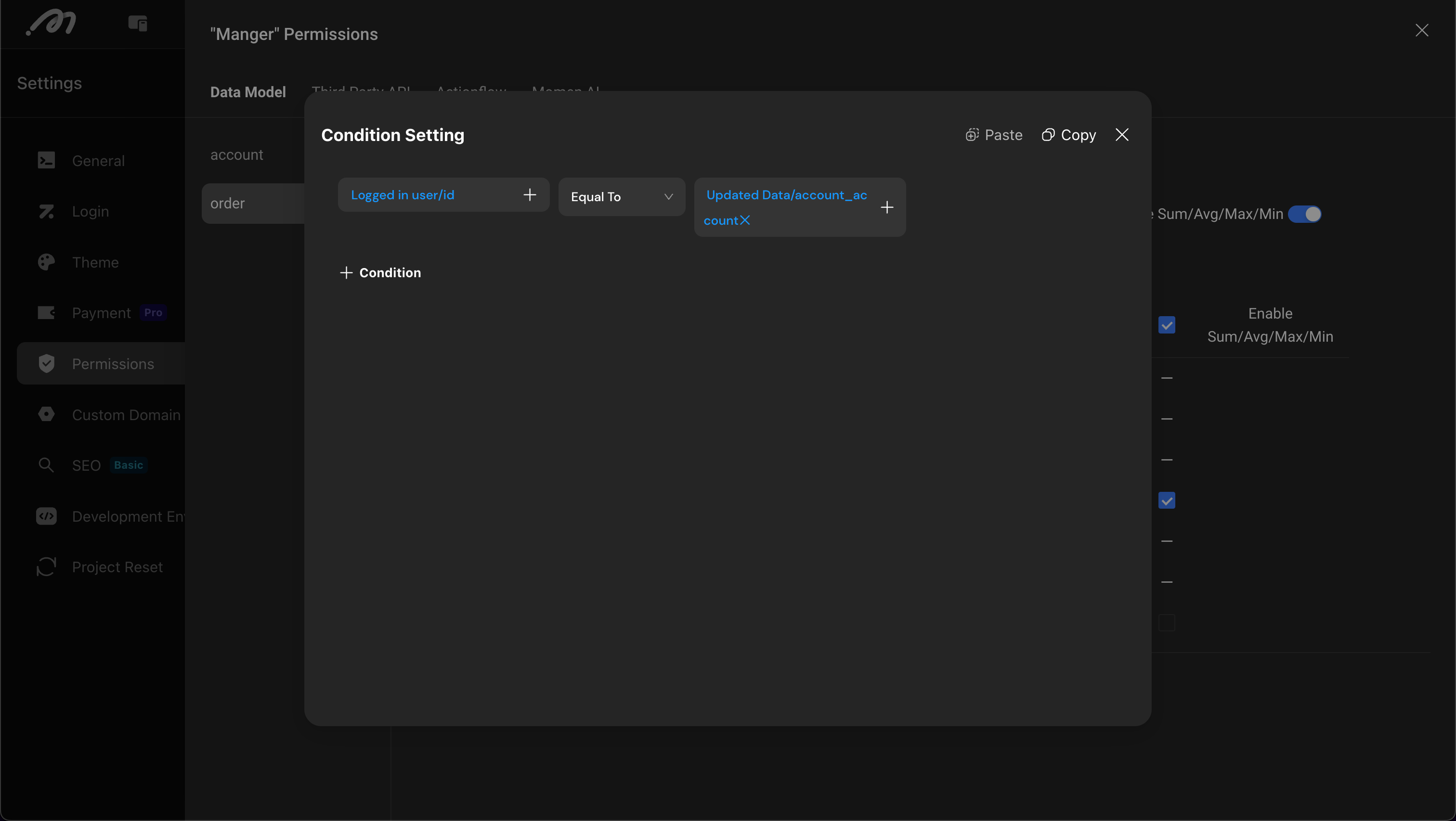
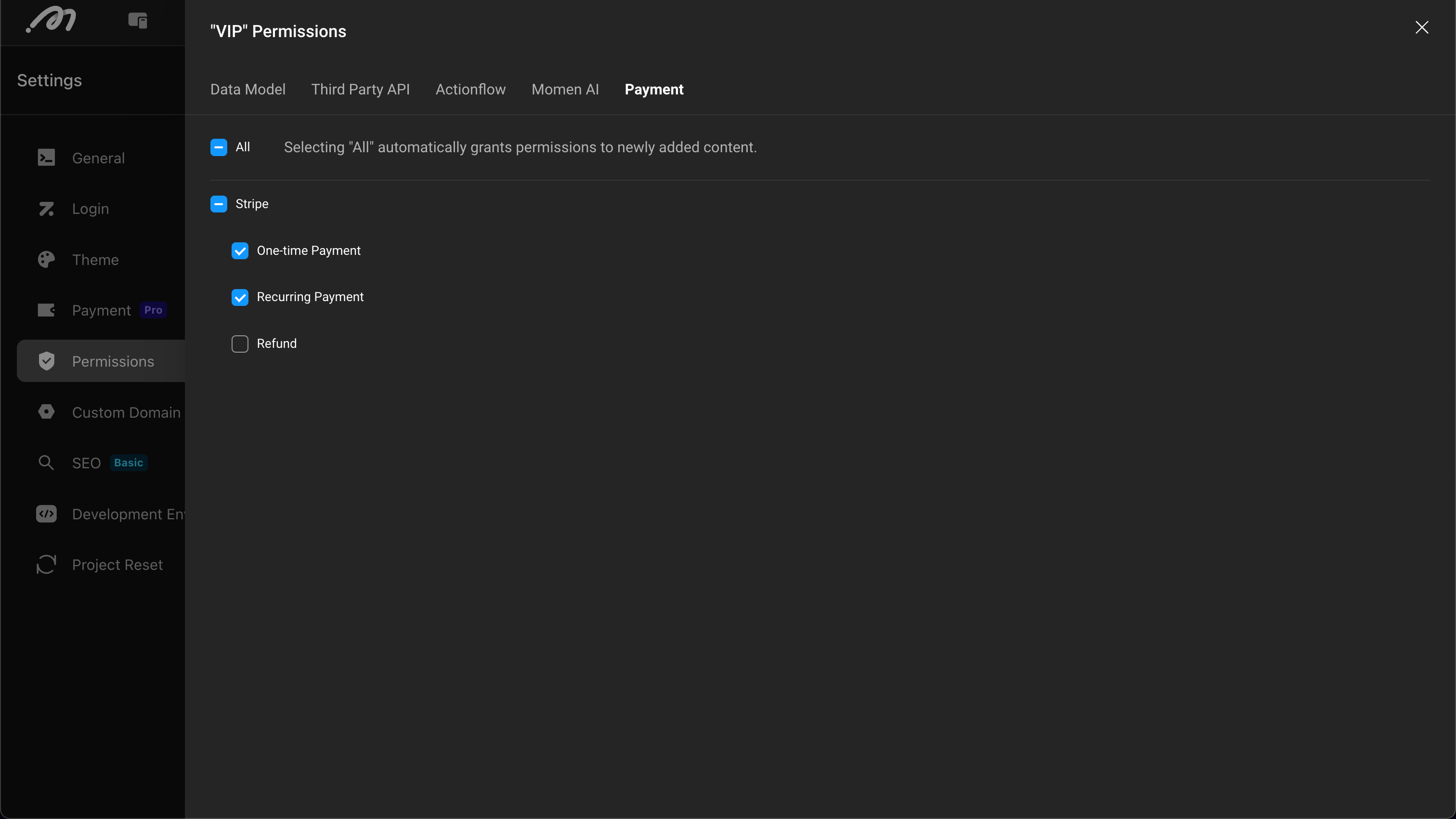
Configure Action Permissions
Controls the action permissions available to users, including APIs, Actionflows, AI, payments, etc.
Except for payments, other actions can add “Advanced Filtering” to achieve more fine-grained control, such as configuring business rules like “Actionflow input parameters cannot be empty”.
Sync Backend
Sync the backend to make the permission configuration effective.
Assign Roles to Users
After completing permission configuration, roles can be assigned to users. Two assignment methods are supported:
-
Manual Assignment: Manually assign roles to users in the permission management system
-
Automatic Assignment: Automatically manage through Actionflows (such as automatically assigning VIP role after purchasing a product)
Role assignment takes effect immediately and does not require backend deployment.
Error Troubleshooting
When a user has no permission to access a resource, the page will show corresponding prompts, and you will see a 403 error in the request similar to the following:
{
"data": null,
"errors": [
{
"errorCode": 403,
"extensions": {
"classification": "TABLE_ACCESS"
},
"locations": [
{
"column": 3,
"line": 2
}
],
"message": "User 1 has no permission for SELECT on order",
"operation": "order",
"path": ["order"]
}
]
}Where:
User 1represents the user with ID1000000000000001has no permission for SELECT on ordermeans the user does not have permission to query the order table
After understanding the error message and locating the corresponding user and specific permissions, you can:
- Check Role Assignment: Confirm whether the user has been assigned the corresponding role
- Verify Permission Configuration: Check if the role permission configuration is correct
- Sync Backend: Ensure the permission configuration has been deployed to the backend and is effective